I touched my keyfob for free bubblegum and they stole my flag :(
Files
What’s going on?
We have keyfob.trace, which is a log file. Firstly, we saw a rfid challenge tag, and we understood what was going on: RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
The keyfoab.trace file is the result of some data generated by a keyfob, a small handheld remote control device that controls a remote keyless entry system.

So how can we read this special file? We searched some hardware tools for RFID security analysis and research, and we found out Proxmark3 was what we needed.
Solution
Thanks to this repo we understand trace command lists the data exchange by the proxmark3 and a tag or a reader in human readable form. Firsly, we loaded keyfob.trace file with trace load keyfoab.trace.
With trace list a table is shown which gives timing information, the src of the data bytes, the transmitted/received bytes itself, a check if the CRC was correct and some decoding of the command.
By accident we discovered trace list 2 gives a better help:
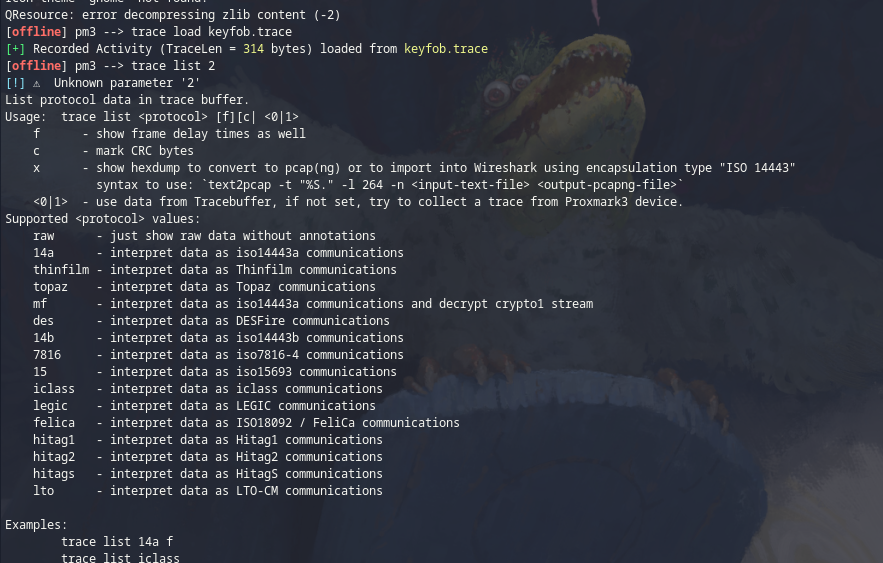
Following the challenge title, we tried trace list mf 1 in order to decrypt crypto1, an unsafe encryption algorithm (stream cipher) and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless smart cards.

We got the flag:
dctf{wh4t_15_g00d_prng_51fb12a0}